India is moving towards Smart Cities and has developed a design and budget to build them. The government has pledged to create an IoT industry in India worth USD 15 billion by 2020, with a possible share of 5-6% of the global IoT (Internet of Things) industry. No doubt, a network of smart cities in any country can boost the national economy and improve the lives of citizens.
A key point to be considered at the stage of designing IoT blueprint is the security of the IoT devices – how can we secure the increased amount of data produced? What’s concerning is India’s IoT policy, developed by the Ministry of Electronics & Information Technology, is still in its draft stage. When you have millions of IoT devices – which could be your connected smartphone, car, home, street lamps, smart grid, water or waste management, the bus you use for daily commute or eGov services – they will share an unimaginable amount of data amongst themselves. While sharing real-time information will help to optimize the use of resources, the increased volume of data can be prone to cyber-attacks, which can wreak havoc on a city or an individual.
However, at what point and how do you secure the IoT? The answer may sound simple: “End-to-End IoT Security”, but it actually takes very meticulous planning and use of state-of-the-art technology.
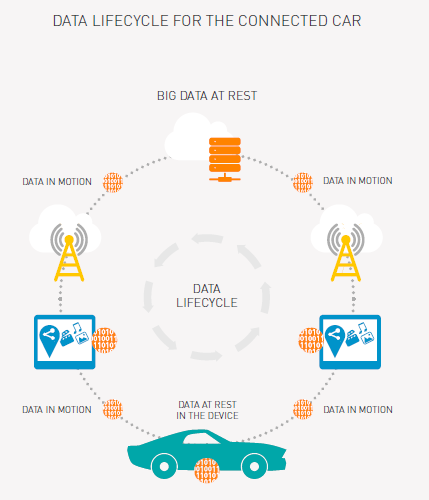
Let’s explain what we mean, using the example of a Connected Car.
- Data in the connected car (in device): Your connected car will have its own digital identity through which it will communicate with other devices under IoT. This identity resides within the device which needs to be kept secure using parts of the IoT application like eSIM and secure communication modules.
- Data in transit (sent to/ from cloud server): The car’s identity data and information collected by it is exchanged between the device and a cloud server through a communication medium like cellular network (2G, 3G or 4G/ LTE). This also needs to be kept secure, and can be achieved through the encryption of data in motion.
- Data at cloud server: Once the data reaches the cloud server, it needs to be kept secure using encryption keys. To make it more secure, these encryption keys can further be secured and encrypted using master encryption keys. For further security, we can have HSM (hardware security modules) for management of these encryption keys.
- Access level: The huge data collected through IoT network will need to be accessed by various people for different types of work. It’s why we must maintain multiple secure access levels, depending on the requirements of different stakeholders, so they can access only the data they need to. This can be done using Identity Access management solutions, while public key infrastructure (PKI) smart cards or one-time-password generator devices, or even digital signature devices can be provided.
To fulfil the dream of smart cities, India needs industry standards for keeping the IoT network secure. Only then can the network of smart cities perform miracles for the government and citizens of any country. You can find out more in our dedicated ebook on IoT Security. If you have any comments, please do tweet to us at @Gemalto_Asia or leave it in the comments box below.


