For global enterprises, security of facilities, data and people is an issue that is increasing rapidly in importance. Whether we like it or not, we live during a time of emerging security threats that force us to go beyond the basics of keeping a written log or simple access management applications. Threats are too complex for traditional security methods now; it’s time for more advanced protection.
There are indeed many reasons why an organization needs to integrate security into their everyday operations, from the costliness of data breaches and property destruction, to brand damage and the potential loss of life. Investing in a healthy security culture can protect the business’ bottom line as well as the safety of their employees, and checking in visitors is the first line of defense.
Several threats can be mitigated by implementing an integrated Visitor Management System (VMS) that secures people, data and infrastructure. Indeed, visitor management systems are improving around the world, but it is important to be aware that there are problems that remain with the majority of existing visitor management solutions:
- In a high traffic situation, it’s extremely difficult for security personnel to keep up with securely processing each visitor while also protecting their identity.
- A VMS that relies on the honor system (trusting visitors to enter accurate information into the system with an iPad-based Self-Check-In process) is not secure enough.
- Reading information from IDs is not secure enough. Security staff need assurance that actual ID verification (with a document reader) gives them; they need to know if people are who they say they are.
Balancing security and the visitor experience

Our combined approach does not see security and the host/visitor experience as mutually exclusive. In our experience, we have seen that a more efficient, convenient and welcoming visitor experience actually leads to better security.
When organizations make following the security plan feel like walking downhill, people are more likely to cooperate, and if the experience is good enough, they won’t even realize they’re doing it.
When it comes to modern solutions for visitor management, you should look no further than Traction Guest – experts in their field and providers of a leading cloud-based visitor management system that delivers an intuitive sign-in experience.
We’re proud to announce we’ve partnered with Traction Guest, setting a new security standard for visitor management by combining their system with our ID scanners.
The partnership
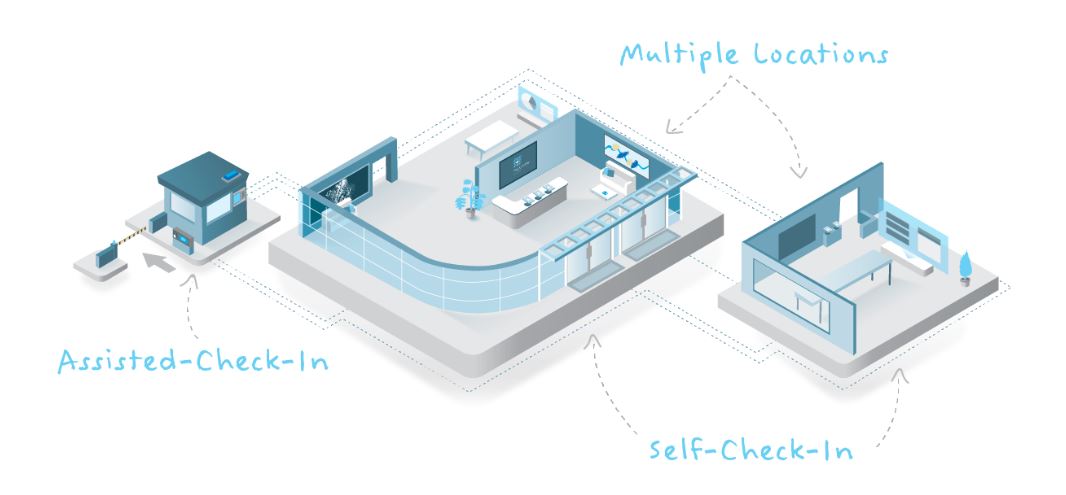
Traction Guest’s platform coupled with Gemalto’s high-end and reliable ID scanners, will enable enterprises to deliver a holistic and secure visitor management experience. Integrating Gemalto’s high-end identity readers with Traction Guest’s visitor management system provides the unique opportunity for our customers to process high visitor volume while also bolstering security and efficiency.
This is perfect for scenarios such as:
- New Assisted Check-In: security personnel with an airport-grade ID scanner to verify (and not just read) government-issued ID at a parking gate, external kiosk, or in the lobby. This delivers a heightened level of security while also speeding up the check-in process. It allows staff to identify security threats well away from the main building and provides an opportunity for staff to help visitors find their way to the correct parking lot, building and office.
- High traffic/large volume of visitors
For example, if a visitor drives up to a security gate a security guard using Traction Guest’s offering (armed with Gemalto Scanners) can verify their ID, make sure they’re on the invite list, screen them against watch lists, print them a badge and notify the host that they’ve arrived. At that point, the guest is either finished signing in or can complete a more detailed Self-Check-In process at an iPad inside.
For more information, make sure you check out the latest details here.


