
Digital transformation and 5G introduce new risks to the confidentiality, integrity and availability of enterprise data. Trust-by-design NFV architecture must prevail.
Let’s have a look at:
- Gemalto’s understanding of the current 5G digital transformation
- Gemalto’s 5G vision
- The best way to ensure a trustworthy 5G network
1. What do you believe is the biggest digital transformation challenge to mobile operators this year?
The biggest digital transformation challenge to CSPs this year is indeed the complexity of the ecosystem that is developing in front of them. We’re going from a very consistent, static model where there was very linear model with vendors supplying to telcos, and telcos addressing their own individual customers. The complexity of this model is going to change especially with the advent of 5G, where we move towards to the digital transformation, and the end-customers of the telcos will indeed become the industry verticals. With that, will come a big cultural divide in such that they speak different languages: CSPs will need to adapt their way of working to address the need of these different industry verticals.
As 5G is the first cellular generation to launch in the era of global cybercrime, indeed trust will have to be inserted into that relationship (between telcos and the industry verticals) in order to build a strong, solid foundation going forward.
5G is the first cellular generation to launch in the era of global cybercrime.
2. What’s Gemalto’s vision for 5G?
Gemalto’s vision for 5G is that it’s truly a platform for digital transformation. 5G will be leveraged by service providers to collect information, to generate actionable insights from that information, to bring it to the cloud and to help automate people’s daily life.
Trust is increasingly perceived as a pervasive transversal factor to be added to a trust-by-design virtualized architecture to help deliver the full 5G promise.
Trust is increasingly perceived as a pervasive transversal factor to be added to a trust-by-design virtualized architecture to help deliver the full 5G promise.
3. How to ensure a trustworthy 5G network?
Gemalto has issued a white paper that looks into the new trust model for the 5G era and covers 5 topics:
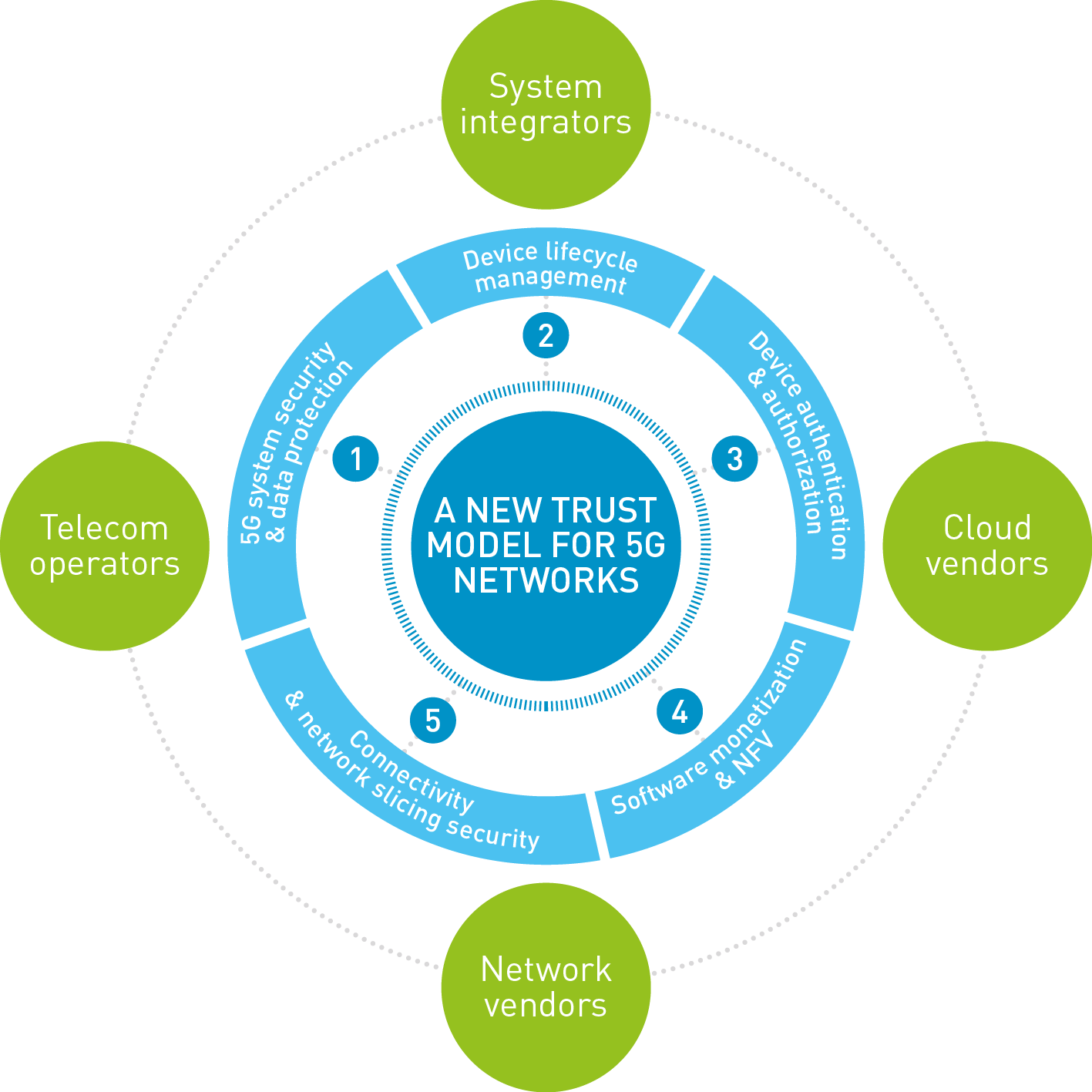
- Data protection.
We believe that as 5G network’s goal is to be able to capture insights, those insights will be gained from processing a lot of different data collected from the billions of IoT 5G-connected devices. All of these insights will be then leveraged in order to improve future actionable insights and to be able to implement predictive analytics. Those predictive analytics will ultimately trigger automated events and help to automate our daily life.
5G network softwarization and virtualization increase the attack surface, thus exposing critical information to lawless hackers. Ensuring data confidentiality, integrity and availability via a proper fabric of trust (e.g. secure enclave, encryption) become of primary importance for all stakeholders (telecom operators, network vendors, cloud vendors, system integrators).
Ensuring data confidentiality, integrity and availability via a proper fabric of trust has become of primary importance for all stakeholders.
- IoT device lifecycle management.
As IoT sensors and many different devices will be in the field for 10 to 15 years rather than our traditional smartphones (which typically last between 2 and 3 years), we need to make sure that we can upgrade the software in each of these devices. So IoT device lifecycle management is extremely important going forward into the 5G system.
- Authentication and authorization of devices connecting to the 5G system.
We need to ensure that the devices which are connecting are authentic, 5G-devices which are authorized for us (users) on the network by the cloud service providers, by the connectivity service providers, by the service providers that are ultimately collecting the data and leveraging it in order to be able to automate our daily life.
- Network slicing.
It’s extremely important that we can correctly isolate the data which is flowing in each of the network slices which are being leveraged by the service providers on the network of the connectivity service provider. Meaning that if we have one slice for an autonomous vehicle and another one for a massive IoT sensor network, then we need to ensure that a Distributed Denial of Service attack on the massive IoT slice wouldn’t bring down a critical service like autonomous vehicles which could potentially have human casualties or even more dire consequences. In order to do that, we have established a collaboration with Intel to leverage their SGX enclave, and that secure enclave is used to protect the keys which are used to authenticate, and to provide confidentiality and integrity protection between the virtual network functions flowing along different network slices. eSIM can play an increasing role in advanced authentication, and in network slicing authentication.
eSIM can play an increasing role in advanced authentication, and in network slicing authentication.
- Software licensing.
Many different software vendors will be contributing to the success of this 5G network. In order to be able to protect everybody’s IP, software licensing technologies can help connectivity service providers and software vendors to jump into a pay-as-you-go or subscription based model around software licensing. What that means is that rather than having upfront fees for each NFV-ized network function that is acquired by a connectivity service provider, we’ll have the possibility to be able to implement those much more linear models so that the telecom operators is truly paying what it needs to use, as opposed to paying upfront for the different software functions that build up the 5G network.
What’s your view about deploying trust-based schemes across virtualized networks? Feel free to react here or on @GemaltoMobile.
Related resource:


