Data Breach Prevention Plans: Cyber Security’s Reality Distortion Field
One of my vices is I like to play poker — specifically Texas Hold’em. I love the flight-or-fight aspect of every hand. It’s fun, but not easy.
The biggest challenges for many players is knowing the difference between a great hand and the best hand. It’s a thin line sometimes. You know without a doubt your pair of Kings is going to win you the hand… and then your opponent reveals three 10s and takes your chips.
What happened? You misread something because you got caught up in your own reality distortion field — the ability to convince yourself of almost anything despite the facts and probabilities. You fell in love with that pair of Kings and you “overplayed” them.
Based on the findings of Gemalto’s latest Data Security Confidence Index research study, it seems many companies are getting caught in cyber security’s reality distortion field and betting far too much on one aspect of security: data breach prevention plans.
Faith in Perimeter Security
Since April 2015, when I analyzed the results of the 2015 Data Security Confidence Index, over 824 million data records have been stolen/lost according to the Breach Level Index (BLI). Since 2013, when the BLI was launched, there have been 3.9 billion records stolen or lost.
However, this year’s Data Security Confidence Index (DSCI) study – which surveyed 1,100 IT decision makers (ITDM) worldwide – found that many ITDMs are still willing to bet a lot on their organizations’ perimeter cyber security.
- Of the ITDMs surveyed, 61% believe their organizations’ perimeter security systems were very effective at keeping unauthorized users out of their network.
- In the last five years, 86% of organizations have increased their investment in perimeter security.
- On average, more than 8% of the respondents’ organizations’ security budget is allocated to purchasing, deploying and maintaining perimeter security technology.
Data Breach Prevention Confidence is Fragile
Based on the responses to other survey questions, we find contradictions that indicate that respondents may not be as willing to trust data breach prevention plans as they think they are.
- 66% of respondents claim that unauthorized users can access their network, with 16% admitting that they could access the entire network.
- 69% of ITDMs are not confident their organizations data would be secure if an unauthorized user penetrated their network.
- Over a quarter (27%) of respondents’ organizations have suffered a perimeter security breach in the last 12 months.
- Both internal (65%) and external (79%) sources were thought to be the cause of respondents’ organizations’ last security breach.
The Cost of a Data Breach
Based on the above, I’m frankly surprised the majority of organizations are still giving perimeter security such overwhelming votes of confidence.
And those breaches are taking a serious toll. When I say that organizations are betting too much on perimeter security, I mean that literally.
- 92% of respondents’ organizations that have been breached suffered commercial consequences as a result.
- In the last five years, organizations that have suffered a perimeter security breach experienced costs of over $1.1million, on average.
- 24% of surveyed ITDMs believe that over 5% of their organization’s IT budget has been lost on detecting and fixing breaches in their perimeter security.
Creating a Balanced Data Security Approach
Data breach prevention is an important part of a security strategy. No one is going to roll out the red carpet for a cybercriminal. But more companies need to recognize that investing in prevention doesn’t necessarily translate to breach preparedness.
Fortunately, there are some promising signs in this year’s DSCI that more organizations are making data security and identity and access control tactics a priority as well — though still not to the extent of perimeter security.
In the next 12 months, 69% of respondents said their organizations planned to increase their investment in perimeter security technology, but 63% plan to increase their investment in data security and 54% plan to do the same for their identity and access control.
While the diversified investments is a good sign, there is still plenty of room for improvement, as most IT decision makers said they disagree with how the security investments are allocated.
If they were in charge of the security budget, 51% of respondents said they would allocate the most budget to data security, with only 32% agreeing they’d invest the most in perimeter security.
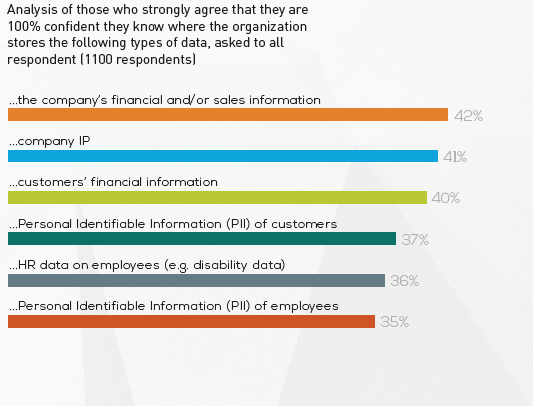
And in order for the data security investments that are being made to be effective, organizations of course need to know where their data is stored. Unfortunately, only 37% of respondents said they were completely confident that they know where their customers’ PII is stored and only 40% know where to find customers’ financial information.
The impact of high-profile breaches has caused 78% of respondents’ organizations to adjust their security strategies, but there’s still a lot of room for improvement.
Perhaps the most disturbing stat from this year’s DSCI for me is this one: Very few (6%) respondents claim that over 10% of data that was most recently breached was protected by encryption.
It’s possible that number remains so low because organizations continue to believe their first line of defense — their perimeter security — is enough; they keep overplaying that pair of Kings.
The questions we should ask now are:
- Are organizations adjusting their security strategiesappropriately?
- Will companies listen to their IT professionals and re-adjust their investments and tactics to better emphasize data security?
In other words, can they see through cyber security’s reality distortion field?
Let’s hope so.

Learn more about the findings from this year’s Data Security Confidence Index by downloading the complete report, and checking out the Data Security Confidence Index 2016 infographic.
You can also visit the Data Security Confidence Index research page for a visualization of many notable DSCI results.