You tuned in and asked some really great questions during our recent webinar, Their Cloud. Your Data. The Global State of Cloud Security (now available on demand). The webinar covered the findings of The 2016 Global Cloud Data Security Study that included adoption trends for IaaS, PaaS and SaaS, the prevalence of shadow IT, the role of data governance, and data security practices in the cloud.
We also shared data security strategies that organizations can follow to take advantage of the business benefits of the cloud, while protecting sensitive applications and data across your cloud environments.
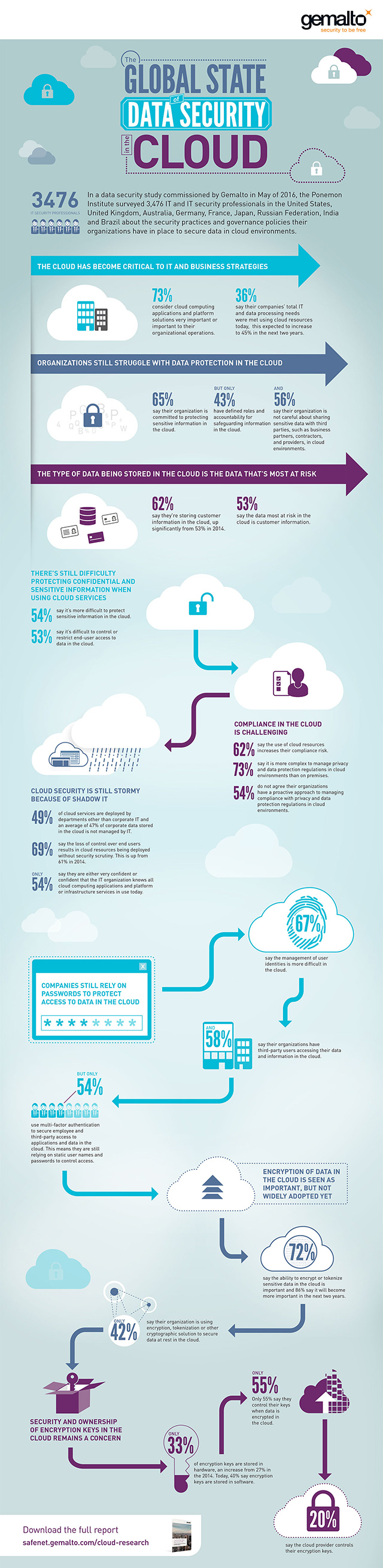
Check out the infographic below for a quick overview of the cloud data security trends covered in the webinar:
At the conclusion of the webinar, we had a number of questions asked by our attendees.
Here’s a quick summary:
Are there specific cloud environments that are more “pro” customer-controlled keys than others?
Just about every cloud environment has the option or opportunity to use customer-controlled keys. The ability to manage and own your keys in the cloud is very important as you have control over who can access your data. If you’re looking for a way to centrally manage, prove ownership of, and secure your encryption keys and data in cloud environments, find out how Gemalto can help you.
Do you think it’s more important for the service provider or the enterprise customer to be in control of security in the cloud?
It’s a balance. However, accountability will always fall to the enterprise customer. While service providers have made great strides to make it easier for people to use security and encryption products within cloud environments, it’s up to you to ensure your data is secure – wherever it goes.
As your organization expands to multiple cloud environments to complete various projects across the enterprise, that’s when you’ll find a need for operational efficiency in your approach to data security. You’ll want to be able to centrally manage and control security and data – both on-premises and in cloud-enabled environments.
What specific support does Gemalto provide for HIPAA requirements?
In terms of HIPAA (Health Insurance Portability and Accountability Act) and other compliance and regulatory mandates, organizations must go beyond basic user access controls and proactively apply strong security and policies.
At a high level, the controls and solutions that you’ll want to use in this type of compliance situation is:
- Multi-factor authentication to control access to cloud-based applications
- Encryption to keep patient and other sensitive data secure and confidential. This includes encryption of data in motion, as well as data at rest in files, folders, shares, virtual machines, and databases.
- You’ll need to underpin this with centralized enterprise key management to maintain ownership of your encryption keys, and hardware security modules to ensure a root of trust.
Want more information about cloud data security trends? Listen to the complete webinar now available on demand and download The 2016 Global Cloud Data Security Study.