
Cloud security concerns hold many organizations back. But they don’t have to, as I’ll cover in this post.
Today your IT team is faced with more security threats, more compliance mandates, and more data to protect. And with business teams across the organization adopting cloud technology on their own, chances are the team is juggling even more isolated requests and projects, too.
There’s no doubt the cloud comes with big benefits. It will help your organization to:
- Get products and services to market faster
- Reduce storage and infrastructure costs
- Provide access to business applications and information anytime, anywhere, and from any device
- Process, analyze, and put data to use sooner
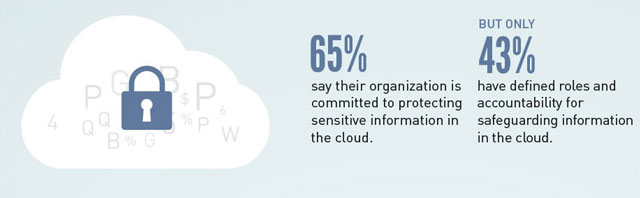
Sure, the cloud helps manage growing data demands in today’s connected and competitive digital world. But what happens when YOUR sensitive data makes its way to THEIR public cloud?
The good news is that you don’t have to say no to new or existing cloud initiatives.
Instead, make sure your team has a plan for addressing these leading cloud security concerns:
- How do we illustrate control of data and maintain compliance in the cloud?
To ensure compliance, organizations must be able to centrally, comprehensively, and efficiently track activities relating to regulated data—even for data in cloud environments. For example, this requires an authentication management platform that enables your company to centrally define policies and control across both on-premises and cloud-based applications and services.
In addition, organizations must have a centralized, efficient way to manage encryption and keys company wide, which streamlines the process of managing and auditing who and what has access to your sensitive data – wherever it goes.
- How do we mitigate data privacy and sovereignty issues in the cloud?
We encourage you to talk to your legal team about this particular cloud security concern. It’s important to know that many regulations are specific to a given region and stipulate where sensitive information assets can and can’t reside. For example, before a federal government agency in the United States migrates sensitive assets to the cloud, the organization will need to ensure the cloud provider won’t store or manage information assets in facilities outside of the country.
Likewise, in some European countries, a healthcare provider can’t use a cloud provider to store patient data unless the provider’s facilities are located solely within the specific country’s borders.
- How do we prevent cloud administrators and other tenants from accessing our sensitive data in the cloud?
Your organization must have a way to guard against insider threats and mitigate the risks posed by malicious administrators. It’s your responsibility to ensure that, even in multi-tenant public cloud environments, your team has the visibility and control they need to safeguard sensitive assets to ensure cloud provider administrators can’t abuse their super-user privileges.
This also applies when a software as a service application uses a cloud provider to host their infrastructure. You’ll also want to enforce separation of duties by requiring different administrators to conduct critical administrative tasks, such as policy changes and key export.

- How do we control what data is accessed in the event of a government subpoena?
In this instance, it’s important to know what’s happening and have control of what data is accessed. If the cloud service provider is subpoenaed and you do not own your encryption keys, the provider will be forced to provide your encryption key to the requestor, whether it’s a government agency or other entity. They may also be prevented from notifying you.
When you own your encryption and encryption keys in the cloud, you or your company may be forced to eventually provide the key, but you will be informed about it and have the opportunity to respond accordingly.
- How do we ensure data is securely decommissioned from the cloud?
When you leave a cloud for another or elect to remove your data from the cloud, you must have a clear understanding of how your data may be retained. Some cloud providers may retain customer data until all debts are paid when a contract is terminated.
You’ll also want to ensure the proper destruction of instances and virtual machine images that may contain sensitive information. Make sure you have an exit plan to leave the cloud with confidence and without a data trail.
- How do we centralize data security across environments?
If you find your organization deploying separate data protection projects to react to different mandates, meet the security requirements of individual business units, or address a security breach, you’re are not alone.
It’s important to take a centralized, unified approach to implementing data security across all of your cloud and on-premises environments. Not only will it improve your organization’s security posture, you can reduce costs and increase business agility.
What is the leading data security concern as your organization moves to the cloud? Let us know in the comments below, and then find out how our data protection solutions can help with your next cloud security project today.


