Cloud Access Management Headaches
Cloud access management is a primary  challenge to using cloud apps securely in enterprise settings. With the proliferation of SaaS, PaaS and IaaS, managing access policies, including strong authentication, for each app provides an IT management burden. Users need to maintain numerous user name and password sets, resulting in lost or forgotten passwords, lost productivity and “password fatigue.” In fact, lost or forgotten passwords account for 20% of help desk tickets.
challenge to using cloud apps securely in enterprise settings. With the proliferation of SaaS, PaaS and IaaS, managing access policies, including strong authentication, for each app provides an IT management burden. Users need to maintain numerous user name and password sets, resulting in lost or forgotten passwords, lost productivity and “password fatigue.” In fact, lost or forgotten passwords account for 20% of help desk tickets.
Furthermore, IT often lacks insight into which users are accessing which apps, and how frequently, resulting in shadow IT and mismanaged resources. In terms of access control, if an employee leaves the company, how can you ensure they can no longer access their apps? Additionally, while it’s possible to secure access to cloud apps with 2FA, IT is often unclear who bothers to do so. Lack of strong user access control results in vulnerability to compromise by phishing, brute force, hacking of cloud databases, and other threat vectors.
Without centrally managed access controls, the use of cloud apps within an organization cannot be scaled efficiently, and results in security holes, high administration overhead, user frustration and organizational inefficiencies.
Cloud Access Management: Identity is the New Perimeter
The Identity Theft Resource Center (ITRC) announced in 2015, “Breaches have become the third certainty in life.” In the face of this new, grim reality, John Fontana writes three thoughts that might help define progress in 2017 and give the good guys a fighting chance against the bad guys. “If identity is indeed the new security perimeter, than the underlying technology for that perimeter must be built on standards.”
SAML Authentication
Enter SAML, Security Assertion Markup Language, an XML-based open standard for exchanging authentication and authorization data between parties. A standard since 2002, SAML is a product of the OASIS (Organization for the Advancement of Structured Information Standards) Security Services Technical Committee. The SAML protocol enables users to log in to their 10, 15, or 25 cloud apps using just one username and password set. This is called identity federation, because instead of having 10 or 25 different usernames or identities, the user need only maintain a single identity. With identity federation, a single SAML-supporting system called a trusted Identity Provider (“IdP”) governs the authentication of users, with cloud apps relaying the authentication process to the Identity Provider each time a user attempts to access them.
SAML-based Identity Federation
Federated identity solves the challenges and frustrations of managing credentials for numerous web apps separately, whether internal or external to an organization. Standards make federated identity possible, and SAML is a key piece of federation architecture, as well as the predominant identity federation standard. Additionally, widespread and growing adoption is a key advantage to SAML.
Because it is XML-based, SAML is a very flexible standard. A single SAML implementation can support single sign-on (SSO) connections with many different federation partners. Interoperability gives SAML an advantage over proprietary SSO mechanisms, as it prevents vendor lock-in, allowing organizations to move from one SAML authentication platform to another, and retain any 2FA tokens based on OATH. The OATH standard, was created by the Initiative for Open Authentication, and refers to cryptographic algorithms for generating one-time password (OTP) tokens.
As testimony to SAML’s flexibility and interoperability, the Kantara Initiative established an interoperability testing program where SAML vendors prove out-of-the-box interoperability with other SAML implementations. To date, The Kantara Trust Registry has certified over 80 solutions from numerous vendors and organizations worldwide.
How SAML Authentication Works
SAML authentication enables the sharing of identity information between an IdP and cloud or web applications. A SAML-based authentication model is composed of an identity provider, which is a producer of ‘SAML assertions,’ such as SafeNet Trusted Access, and a service provider, which is a consumer of assertions, such as G-Suite, Office 365, and any other cloud app that supports SAML. SAML assertions are generally signed with a PKI signature which confirms that the assertion is authentic.
An authentication service acting as identity provider collects the user’s credential and returns a response to the cloud app being accessed. This response is called a SAML assertion. The SAML assertion contains an accept or reject response. If the SAML assertion is valid, the user is logged in.
Key to enabling SAML-based identity federation is mapping users between the IdP and service provider, so when a user accesses Office 365, Office 365 knows to redirect them to the IdP for strong authentication.
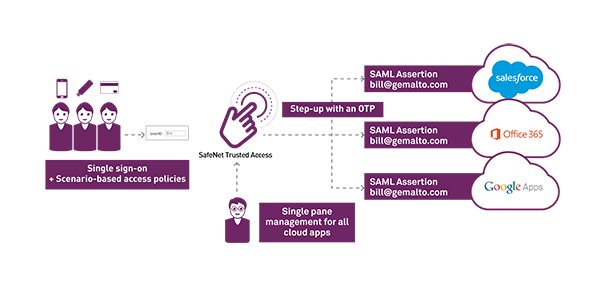
Identity Federation for Centrally Managing User Access Control
SAML can be used to extend users current enterprise identity to cloud applications. Federated authentication can completely eliminate the need for users to remember multiple user name and password combinations. Users log in with the same enterprise identity throughout all their cloud apps, meaning the same identity they use to log in to the network every morning.
From a users’ perspective, SAML-based identity federation is seamless. SAML works using a cookie, so a user who’s logged into Office 365 will not need to re-authenticate if they open other cloud apps in a new tab, such as Dropbox, WordPress, Salesforce, etc.
Benefits of SAML-based Identity Federation
In addition to eliminating the aggravation of password fatigue for users, SAML authentication enables IT administrators to manage a single credential set per user for all apps. When users leave the organization, IT must revoke just one credential set, not five or seventeen. Credentials can be revoked without logging into each separate cloud app. Automated workflows can further minimize lifecycle administration overhead when synched with user stores such as MS SQL or Active Directory.
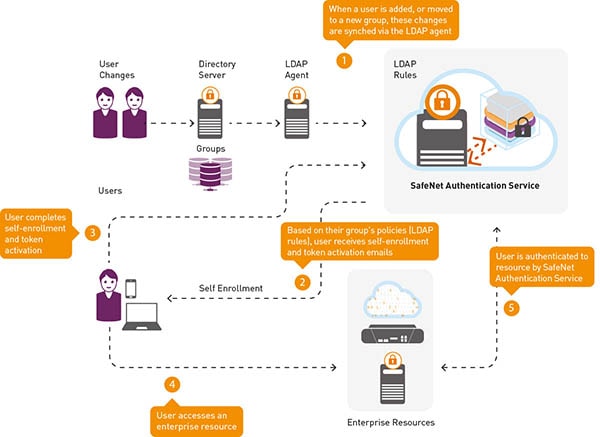
SAML for Cloud Access Management and User Access Control: Who Needs It?
Who needs SAML? Anyone who’s managing users accessing cloud apps and wants to do so in an efficient, secure and scalable manner. If that sounds like ‘everybody in IT,’ well, perhaps that is the case. Web apps have been pervasive for many years now. There are probably few enterprises not leveraging them in some way.
If your IT infrastructure were a physical space, SAML-based identity federation enables easy movement throughout. Rather than having your employees use one badge to gain access to the building, and another to gain access to the conference room, another for the restroom, another for [OK, you get the point] a single set of credentials ensures smooth, continuous access.
To learn more, view our webinar on-demand, “What is an Identity Provider and Do You Need One“, download the fact sheet on managing the new Identity Perimeter, or watch how to set up an Identity Provider for Single Sign-On in minutes, right below:


