How enterprise and consumer identities are merging
Over the past years, enterprise and consumer identities have been slowly but surely merging in terms of the level of security they offer, the usability expectations they address and their incremental interoperability. This blog drills down into how these different realms are becoming more similar to each other.
Multi-Factor Assimilation
How are consumer and enterprise multi factor authentication methods becoming increasingly similar?
While some two factor authentication methods were created for the consumer realm and then adopted into the enterprise, others were created for the enterprise and adopted for consumer use cases.
- Biometrics include fingerprint scanners and iris scanners built into native apps for consumer or enterprise authentication. The biometric 2FA bracelet called the Nymi band uses your heartbeat rhythm to authenticate you to resources when worn on your hand.
- Context-based authentication is best known in the consumer world as a “Remember me on this device” checkbox or as your Verified-By-Visa (VBV) and MasterCard SecureCode (McSc) password. When logging in from an unfamiliar device-browser pair to a consumer or enterprise service, the user is asked to step-up authentication with an additional factor (such as an OTP). In eCommerce and eBanking transactions which use the 3-D Secure standard, authentication is stepped up during suspicious ecommerce transactions by asking consumers for their VBV or McSc password.
- Single-tap push authentication lets you authenticate with a single tap of a button on a mobile device, and is offered by both consumer services (e.g. webmail) and enterprise authentication services.
 Single Sign On at Work and at Home
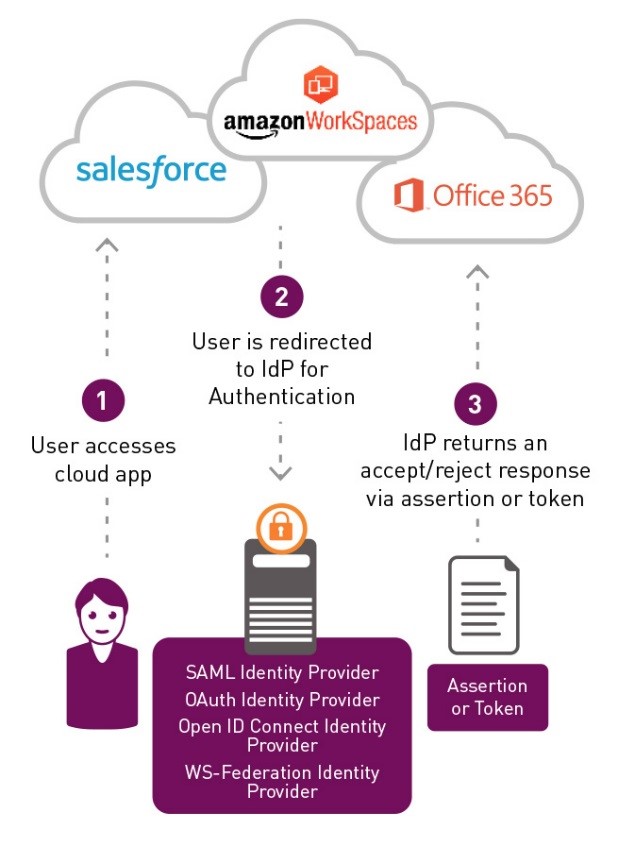
Single Sign On at Work and at Home
The US National Institute for Standards and Technology, better known as NIST, found that its employees authenticate 23 times within a 24-hour period. A key takeaway of its study was its clear-cut recommendation for organizations to implement Single Sign On, or SSO, solutions, wherever possible. SSO order to eliminate password fatigue and frustration.
To quote Gartner, “Single sign-on (SSO) provides the capability to authenticate once, and be subsequently and automatically authenticated when accessing various resources. It eliminates the need to separately log in and authenticate to individual applications and systems, essentially serving as an intermediary between the user and target applications.”
In the enterprise world, an SSO experience is created using password vaults or identity federation protocols such as Kerberos, SAML and Open ID Connect. In the consumer world, federated authentication, a predecessor to SSO, dominates, though consumer-facing password vaults are available, too. When you click the “Sign in with Google” button to login with your current Google identity, that’s the Open ID Connect protocol extending your Google identity to a new, unaffiliated website, removing the need to create a new identity and log in with a new username and password set.
A recent global Gemalto survey, the Authentication and Identity Management Index found that 88% of IT decision makers have already implemented SSO or are planning to within the next two years.
Interoperability – The Key to a Universal Identity
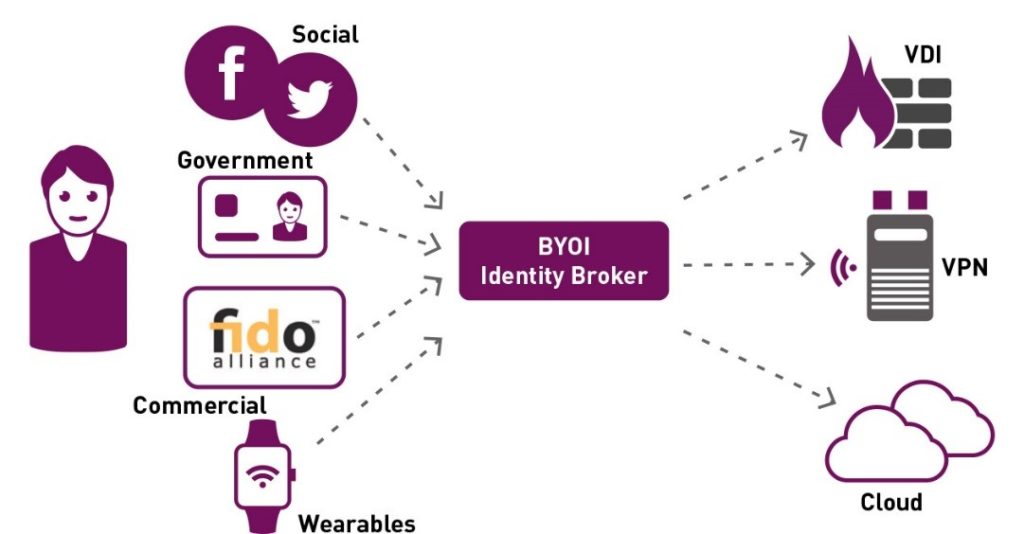
If I start a new job tomorrow, can I start accessing the network, VPN and some cloud apps using one of my social media accounts? If my new job has implemented an identity broker, then the answer is “Yes!”
Similarly, if your organization has an identity broker, you could let your business partners log in to your partner portal using a social identity they already have, saving them the trouble of maintaining a new identity for that service—a worthy cause considering that many breaches are perpetrated by leveraging suppliers’ and partners’ login credentials, as in the Target breach.
An Identity Broker is a system that can support Bring-Your-Own-Identity (BYOI) schemes by taking a user’s existing identity and allowing them to authenticate to unaffiliated websites using that identity. With identity brokering, a single user account can be linked to identities from different identity sources. This is done using protocols such as SAML 2.0 or Open ID connect specifically set up for a brokering scenario.
In the future, we may see an increasing number of identity providers that not only support isolated enterprise identities, but rather providers that increasingly support numerous external identities, such as social media accounts, healthcare smart cards, commercially acquired identities, such as FIDO, as well as identities created with off-the shelf wearables that are embedded with smart card chips.
This kind of identity brokering will make our current identity – a universal one.
And actually – a universal online identity is exactly what the FIDO Alliance is aiming for. A universal identity that is interoperable across consumer and enterprise domains. FIDO – or fast identity online – is an industry wide initiative for establishing a universal strong authentication form factor that consumers will be able to use for both consumer and enterprise services. FIDO is led by strong industry players such as PayPal, Microsoft, Google, ARM, Lenovo, MasterCard, Bank of America, American Express, and the list goes on. The idea behind FIDO is that by leveraging PKI authentication, we’ll be able to use the same USB dongle, biometric eyeprint, Bluetooth authentication token, or mobile device to login to our bank accounts, access cloud apps and sign in to our social networks.
To learn more about the changing face of consumer and enterprise security, watch Digital Identities: The Changing Face of Consumer and Enterprise Security Webinar or download the IAM Trends and Enterprise Mobility eBook.


