
With April upon us, one of the spring cleaning efforts for enterprises is getting ready for the looming GDPR deadline of May 25, 2018. That’s the new General Data Protection Regulation (GDPR) that requires companies to be more accountable to their EU-based users on how their data is controlled and used. It also requires companies to notify their local data protection authority regarding suspected data breaches.
Back to (GDPR) Basics
- The General Data Protection Regulation (GDPR) (Regulation (EU) 2016/679) was created to strengthen the safeguards around personal data and create a more uniform standard within the European Union (EU).
- It was created by the European Parliament, the Council of the European Union and the European Commission.
- Its objectives are to increase protections for personal data, set strict penalties for non-compliance and extend regulatory powers beyond EU borders.
- It affects any organization, regardless of its location, that handles personal data of EU citizens.
- Organizations will need to verify the legitimacy of user identities and transactions, and to prove compliance.
- Companies have 72 hours to notify authorities if there is a data breach
- All companies can be fined, anywhere in the world. If there is a data breach, the maximum fine is 4% of the company’s global turnover or 20 million Euros (whichever is higher!).
GDPR compliance is an enormous undertaking, with a few articles specifically relevant to Identity and Access Management. For example:
- Article 5 details personal data processing, and requires data to be secured from unauthorized access and loss. This can be achieved with Access Management through multi-factor authentication and access policies. In this way, you can set access policies so that only authorized users can access certain resources, and elevate trust using strong authentication.
- Article 24 says organizations must take reasonable security measures responding to potential risks and threats. This applies not only to the data, but also requires solutions that restrict access to corporate networks, protect the identity of users and ensure that they are indeed who they claim to be. Here again, access management and strong authentication can help manage the risk of unauthorized access.
- Article 32 discusses the need for additional security of processing. Enterprises should consider the risk regarding data loss and unauthorized access. Access management solutions enable restricting access to sensitive data, and reduce the risk associated with privileged user access, such as access by administrators and executives.
Proactive GDPR fine reduction
Although GDPR can fine organizations for data breaches, these fines may be reduced if the organizations can prove that they have deployed security controls to minimize damage. Whereas some GDPR-ready articles have focused on the data protection element of GDPR, the identity protection part of GDPR seems to be overlooked: because when it comes to preparing your organization for GDPR, identity and access management provides a first line of defense to the sensitive user data harbored in your companies’ cloud and web apps.
Cloud compliance and access management
One of the challenging issues for enterprises preparing for GDPR compliance is the special nature of accessing cloud-based applications. As you would expect, data located in the cloud is more vulnerable to data breaches due to the inconsistent—and often inadequate—access controls applied to cloud and web access. According to Gemalto’s 2018 Identity and Access Management Index, 42% of the survey respondents felt that cloud apps may be targeted for cyber attacks due to poor cloud access management solutions. Whereas some cloud-based apps offer basic context-based and two-factor authentication, others offer none at all. According to a recent joint research study by the Ponemon Institute and Gemalto, enterprises today use on average 27 cloud-based apps for their employees’ day to day work. However, in most organizations, no mechanism has been instated to allow for centralized access controls to these cloud apps. Nonetheless, cloud access management security solutions are catching on, with two-fifths of IT decision makers already managing SSO centrally for all their applications and another 50% wanting to do so in the future.
Access management allows organizations to effectively ensure policy-based access controls to a company’s cloud and web-based resources. To ensure that only authorized users can access sensitive data belonging to EU citizens, for example, contact details, shopping and purchase history, PII, etc., IT and security professionals need the ability to centrally define and enforce access policies, as well as ensure visibility into who is accessing their apps, when, and how their identity is verified. To that end, an effective access management solution is more than a reporting tool: it is a solution that helps enterprises manage and secure access to any cloud or web app, providing different policies according to the assurance risk.
Leveraging access management to protect EU citizen data
To address specific use cases, policies can be set up so that only authorized personnel can access personal data belonging to EU citizens, elevating assurance with multi-factor authentication after a single sign-on session is launched for the appropriate user groups, resources and applications. For example, Sales, Accounts Payable or other user groups that need to access EU citizen’s data (for example, data in a CRM) may be required to step up authentication—after launching a single sign-on session—each and every time they access an app holding this sensitive data in order to demonstrate that mechanisms were instated to mitigate risk and ensure that only authorized personnel accessed it.
Similarly, you can define stricter access for remote workers or contractors, or step down access for low-risk apps.
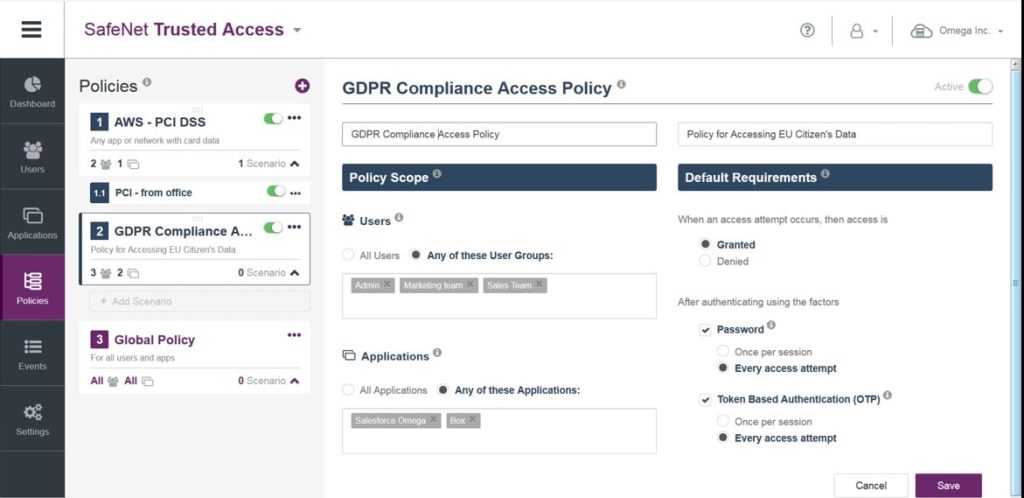
For example, you could set up a policy specifically for GDPR Compliance. Single Sign On could be offered to most of your cloud and web apps, with elevated trust required to access apps containing data of EU citizens.
Addressing this scenario, IT administrators could require password-only authentication for non-sensitive apps, but prompt users to enter an OTP, or approve a login request pushed to their cellphone, for more sensitive apps or scenarios. IT administrators could also define, within this policy, elevated controls on certain geographical locations, requiring stronger authentication from countries outside corporate headquarters.
‘General’ single sign-on is a GDPR red light
Using Single Sign On without the ability to step up authentication within an SSO session creates a ‘general’ or buffet-style checkpoint for all users within an organization and will make demonstrating compliance with GDPR difficult.
Whereas buffet-style single sign-on vets users just once at the entrance, and then offers unfettered access to all apps, a sophisticated single sign-on solution will also let you step-up authentication after launching an SSO session, in order to elevate trust and demonstrate compliance with mandates that require strong authentication and authorization.
With scenario-based policies and convenient access management, not only will you be prepared for GDPR and save your enterprise from costly fines or sanctions, but you will also help prevent identity theft of the most sensitive data within your organization.
Check out this flyer for more information on leveraging access management for GDPR compliance, or download the fact sheet on Matching Risk Policies to Real-Life User Needs. To watch cloud-based access management in action, join a 30-minute live demo webinar of SafeNet Trusted Access.


