This week sees the start of Infosecurity, one of the world’s biggest security conferences held in London. Is it coincidence that we recently saw the effects of a major security breach, making headlines all over mainstream news sites? Unfortunately, the truth is that security breaches don’t just happen in tandem with security conferences, but are continual.
To avoid breaches, we need to make sure we stay a step ahead of hackers, fraudsters and others actively trying to break security measures. In addition, we need to protect organizations and companies from these criminals – as well as from inadvertent or unintended security lapses. So here’s a list of top ten tips to help achieve network security, arguably one of the first areas for a security breach to strike at.
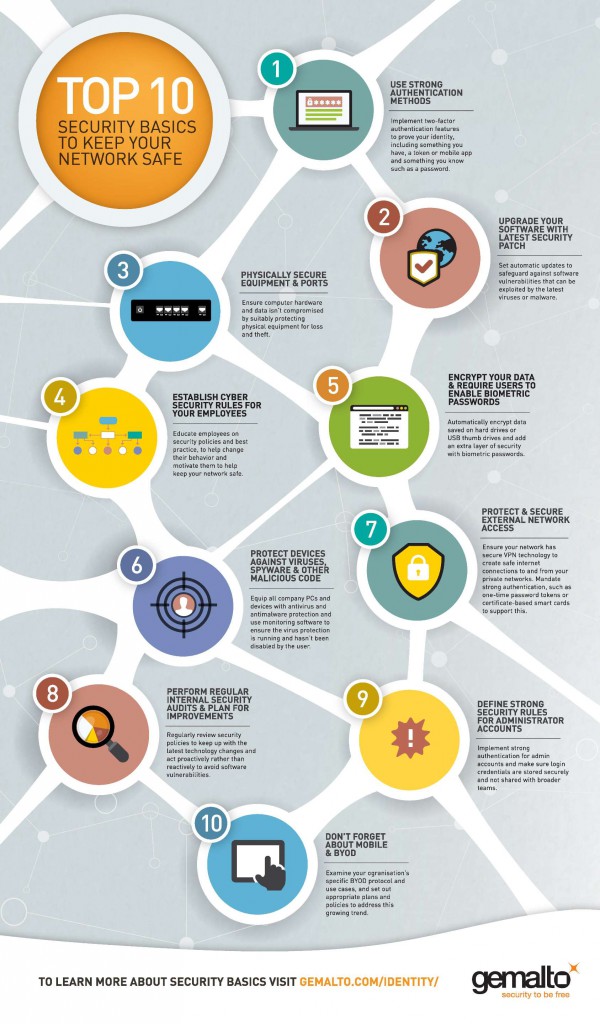
1. Use strong authentication methods
With stolen credentials the culprit in four out of five of security breaches, it’s clear traditional user names and passwords are not secure and no match for today’s sophisticated hackers. Strong authentication is also referred to as two-factor authentication because you have to use two different things to prove your identity. It combines something you have, the authenticator (token, smart card, mobile app), with something you know, your login ID and password.
2. Upgrade your software with latest security patch
No matter how big or small the fix, software security patches are important. A machine that is not updated with the latest security fix is much more likely to have software vulnerabilities that can be exploited by the latest virus or malware. Set automatic updates and educate your employees to accept the updates when prompted.
3. Physically secure equipment and ports
Thieves want more from a corporate laptop than just the cost of the hardware. One single stolen device can lead to sensitive company data, customer records and more. If your computer equipment is not suitably protected, it is easy for criminals to either steal data or infect your computers and network without needing to go online.
4. Establish cyber security rules for your employees and make them aware of the important role they play in security
Regardless of size or number of employees, every company needs a security policy. Ensure employees know the policy and are adequately trained to do what it asks – for example, if you require a BIOS password, ensure your employees are trained in how to set one up. By teaching employees good security practices, you will help change their behavior and motivate them to adhere to your policies. Make sure your employees learn the security policy and you enforce the rules.
5. Encrypt your data and require users to enable bios passwords
An easy way to add an extra layer of security is to enable a password on boot. If a user laptop is stolen, the thief can still access the hard drive by booting from a different disk. With a BIOS password enabled, the hard drive is inaccessible. For most large organizations, the operating system of choice is the enterprise edition of Windows, which includes the Bitlocker drive encryption system. Once set up, this utility automatically encrypts any data saved to the hard drive or USB thumb drives.
6. Protect devices against viruses, spyware, and other malicious code
Equip all company PCs and devices with antivirus and anti-malware protection. Use monitoring software to ensure the virus protection is running and has not been disabled by the user and does not allow non-compliant systems to access your network.
7. Protect and secure external network access
Ensure your network is using securedvirtual private network (VPN) technology to create secure Internet connections to and from your private networks. Mandate strong authentication, such as one-time password tokens or certificate-based smart cards for users to connect through VPN. Make sure your firewalls are configured correctly. Gartner Research found that 95% of firewall breaches are due to misconfiguration, rather than a flaw within the firewall itself, so it’s important to regularly review your firewall logs and make adjustments as necessary.
8. Perform regular internal security audits and plan for improvements
Technology changes so rapidly that associated security policies must be reviewed much more often than other business processes. New software vulnerabilities are discovered daily, so it’s important to be proactive rather than reactive. Regular security audits, at the very least on an annual basis, will help you measure your organization’s current security policy and operations against potential threats.
9. Define strong security rules for administrator accounts
A single factor of authentication is hardly secure, but even worse when privileged admin accounts are shared because of the sheer volume of the number of logins needed to maintain a typical enterprise infrastructure. Implement strong authentication for admin accounts and make sure login credentials are not shared.
10. Don’t forget about mobile and BYOD
With the continuous growth of mobile usage comes demand for employees to use their own devices to connect to your corporate network. While the BYOD (bring your own device) trend will continue to be fueled by user demand, it presents both opportunities and challenges. Tightly examine your organization’s specific situations and use cases and set appropriate policies to address this growing trend.
The network is but one part of an organization’s infrastructure, but is arguably also the backbone due to the connectivity to all other ports to company information and sensitive data. To find out more, visit us at Infsecurity this week (Stand D31) or hear more about how to protect your boss at the conference on Thursday.