Evaluating the Integration Ecosystem of an IAM Solution
What is Identity and Access Management (IAM)?
According to Gartner, Identity and Access Management (IAM) is the security discipline that enables the right individuals to access the right resources at the right times for the right reasons.
IAM solutions provide a methodic framework for granting and requesting access to applications along with enforcing access controls and ensuring visibility into access events.
The focus of this blog is the integration ecosystem of Cloud Access Management and PKI credential management solutions.
Implications of your IAM solutions’ integration ecosystem
There are clear benefits to managing IAM centrally for all applications, be they web portal, cloud-based services, VPNs or virtual environments. According to a recent Gemalto survey, organizations on average protect 3 to 4 applications of each type with two-factor authentication (2FA). Given the numerous management complexities that arise from a fragmented IT environment, it comes as no surprise then that 94% of IT decision makers would like to be able to manage two-factor authentication centrally for all the applications in their organization.
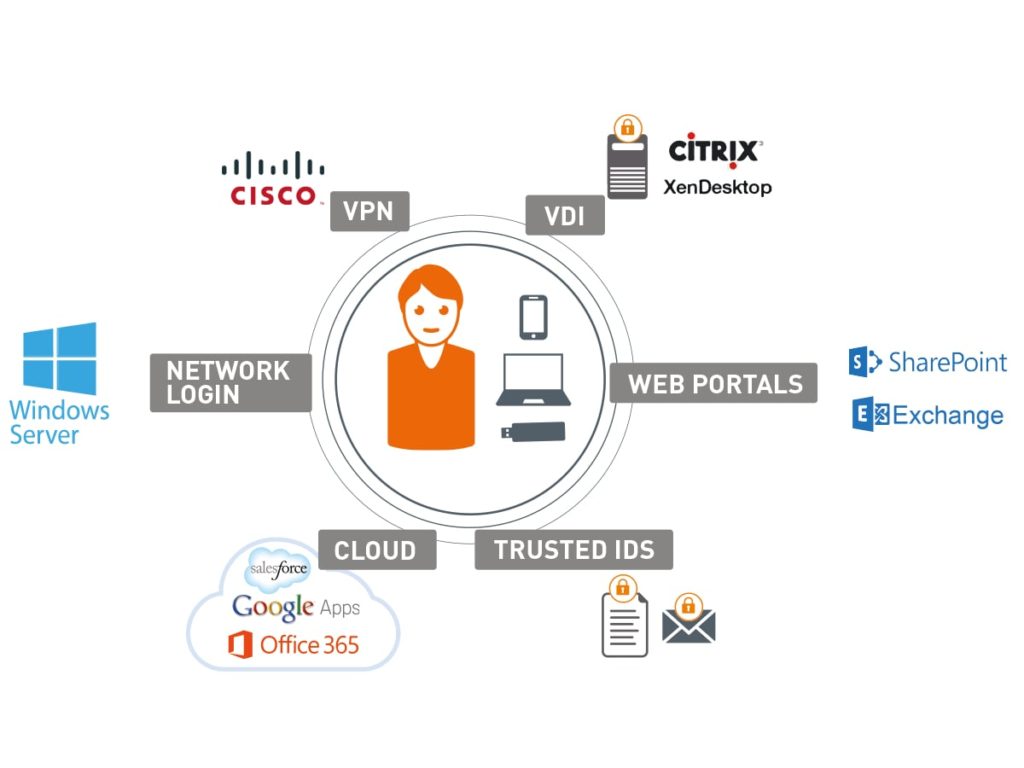 By ensuring your Identity and Access Management solutions’ integration ecosystem is as broad as possible, you are paving the path for a smooth, quick and cost-effective implementation of whatever IAM functionality you’re looking to gain, be it PKI credential management, cloud identity management or cloud SSO. A pre-integrated and validated solution spares your IT department the need for additional development and subsequent performance issues.
By ensuring your Identity and Access Management solutions’ integration ecosystem is as broad as possible, you are paving the path for a smooth, quick and cost-effective implementation of whatever IAM functionality you’re looking to gain, be it PKI credential management, cloud identity management or cloud SSO. A pre-integrated and validated solution spares your IT department the need for additional development and subsequent performance issues.
Use cases supported by IAM solutions
When checking the breadth of a prospective IAM solution’s integration ecosystem, it helps to evaluate it against specific use cases and resources you are looking to support, as exemplified below.
PKI Credential Management and Advanced PKI Security
Use cases supported by PKI certificated-based smart cards and tokens include:
• Digital signature – Based on PKI credentials, these enable proving that a document, transaction or email were signed.
• Email encryption – Protects email from being read by entities other than the intended recipient.
• FDE – Full-disk encryption (FDE) encrypts data on a hard drive so that it cannot be understood by anyone who doesn’t have the key to decrypt the data.
Identity and Access management Use Cases
Use cases supported by IDaaS and cloud access management solutions include:
• Cloud SSO and secure access to cloud apps, such as Salesforce, Office 365 and AWS, etc.
• Local network access, such as secure Windows Logon
• Remote network access to VPNs and security gateways
• Secure access to virtual desktop infrastructure, e.g. Citrix XenApp
Ensuring a future-ready IAM framework
Solutions that support industry-wide standards enable you to meet current, upcoming and evolving business needs.
Some examples of these standards include:
• OATH – An open reference architecture for implementing strong authentication, produced by an industry-wide collaboration of security vendors for the universal adoption of strong authentication. The standards includes widely used algorithms for generating one-time passcodes.
• APIs – These enable integrating with custom applications (legacy apps that do not support SAML, RADIUS, etc.).
• SAML – An open source protocol, produced by the OASIS standards consortium, for integrating cloud apps using a central, trusted identity provider
• RADIUS – Commonly used by VPNs and security gateways, RADIUS (Remote Authentication Dial-In User Service) is a client/server protocol and software that enables remote access servers to communicate with a central server to authenticate users and authorize their access.
Looking to expand your integration ecosystem? Check out our Identity and Access Management ecosystem wheel or locate Technology Partners relevant to your needs.
For more information on IAM solutions, watch How IAM Works in the Cloud or download the Access Management Handbook.


